Phishing attack attempts to avoid URL scanning-based detection methods
Phishing is a cyber attack that uses email or text to go after a potential victim. In a phishing attack, the attacker pretends to be a trusted contact and hopes the victim clicks on the spam link provided in the email. This is an attempt to steal sensitive information from the victim’s computer. Over the years, the attackers have come up with more sophisticated types of phishing attacks forcing organisations to strengthen their defences,
On the 7th of September 2022, we detected a new interesting technique used by a phishing attack to attempt to avoid URL scanning-based detection methods by redirecting to a random Wikipedia page. On the surface, the email seems like a generic password expiry phishing attempt which tries to convince the user that their password is expiring on that day and requests they access the link in the email.
This link is formatted as follows, “hxxp://COMPANYNAME[.]chasingpostcards[.]com/cGhpc2hpbmdAYXR0YWNrLmNvbQ==”. In the URL path a base 64 encoded email address is provided, in the URL example above the decoded address is “[email protected]” which is used to format the phishing pages layout when a user clicks their customised link.
Using a URL scanning service on the “hxxp://COMPANYNAME[.]chasingpostcards[.]com/cGhpc2hpbmdAYXR0YWNrLmNvbQ==” URL, you’ll see that the chasingpostcards website redirects to a Microsoft related Wikipedia page such as “https://en.wikipedia.org/wiki/Microsoft_365.” The chasingpostcards link will redirect to Wikipedia if scanned by an automated URL scanner, this is a method of avoiding detection as if a URL scanner cannot access the intended phishing page it will not report back that the links are suspicious.
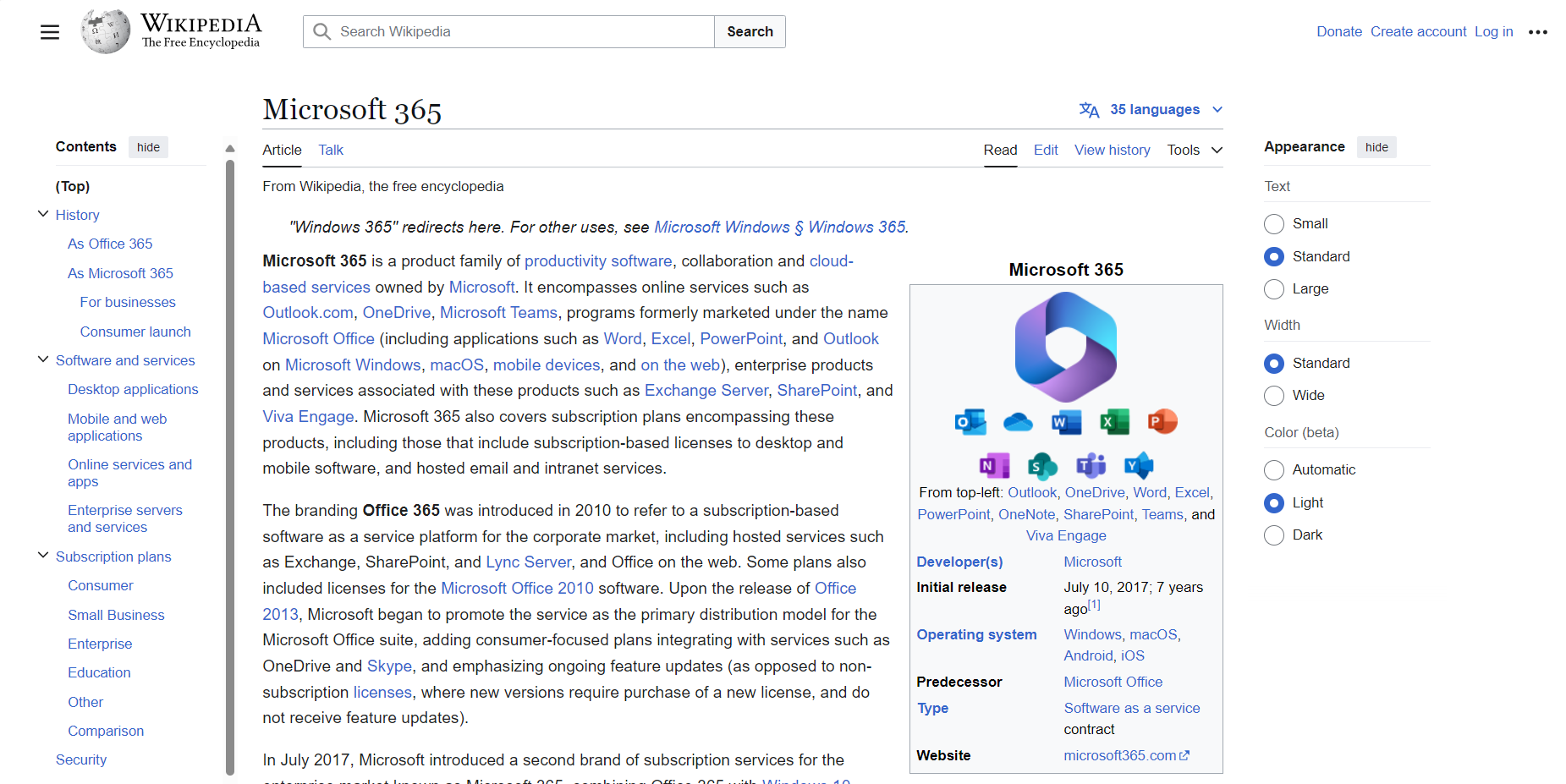
Interestingly when accessing the “hxxp://COMPANYNAME[.]chasingpostcards[.]com/cGhpc2hpbmdAYXR0YWNrLmNvbQ==” link from a local sandboxed environment, we get redirected to “hxxp://moneypro[.]in/O/ cGhpc2hpbmdAYXR0YWNrLmNvbQ==” a page containing a reCAPTCHA which is used to prevent bots from accessing the fake M365 phishing page.

The chasingpostcards address is used as a gateway to prevent detection by automated scanning tools, this is done to use various methods to define whether the access is a “legitimate” user or a scanner such as browser fingerprinting and IP address lookup. After completing the captcha, we are greeted with a fake M365 phishing page.
On this fake M365 login page there is a JavaScript script that can detect any user input without them clicking sign in. This method could capture a user’s passwords if they were to input the password into the field and then realise the site is not legitimate without clicking sign in. This could lead the targeted user to think they are safe and not compromised because they did not click sign in however this is not the case.
Key tips to protect yourself from a phishing attack
This phishing attempt highlights the ever-evolving tactics cybercriminals employ. While the technique used here has been observed, it’s important to remember that attackers are constantly innovating. Here are some key takeaways to keep you safe:
- Don’t click on suspicious links: Phishing attacks are always tempting and they can lure you into clicking on suspicious links. It is important that you analyze all the links you click on and stay away from any links that look suspicious.
- Be aware of unfamiliar senders: While going through your inbox be aware of any emails sent from addresses you don’t recognize. Sometimes attackers pretend to be organisations that you trust which makes it easier to be fooled by unfamiliar senders.
- Verify information independently: A lot of the times, information given in a phishing email is not correct and this can be verified by directly contacting the organisation the attacker is pretending to be. This will give you the confirmation if the email is a phishing attack or not.
- Scrutinise Email language: Phishing emails are not always the best-written emails. These emails might have grammatical errors and typos that you need to be on the look out for.
- Subscribe to our MDR for Email Service: Our MDR for Email service was able to detect this using a multitude of signals. For example, the language used in the email, was similar to the language of other Credential Theft emails, the SMTP server’s IP address was also marked as suspicious due to being associated with other emails that were marked as phishing by other Analysts on our service. Finally, the email address sender name is similar to a sender name already in the targeted user’s contacts. Through this, our MDR system can offer you complete email phishing protection.
By staying vigilant and employing these security measures, you can significantly reduce the risk of falling victim to phishing scams. Remember, if something seems too good to be true, it probably is. If you have any questions about phishing attacks and how to keep your business safe, reach out to us via our live chat.


